How BAC(Broken Access Control) got me a Pre Account Takeover

Introduction:
Hey Hackers!!!
This is a writeup about one of my recent findings on a VDP. I found a Broken Access Control bug which was eventually leading to Pre-Account Takeover. Lets head on to our main story…
Story of the Bug:
It was a typical, boring and unexciting Saturday, I was looking for something to kill the time. So, I decided to do some bug hunting. With the help of this Bug Bounty Google Dork list I found a program to test my skills.
When I signed up on the web application, I discovered some interesting features like creating groups and inviting users. As a bug hunter, it felt like stumbling upon a treasure chest of possibilities, I started manually hunting for Vulnerabilities in Password Reset and 2FA Functionality but I got nothing there. So I went for User Manager option to test without wasting any more time.
Next, using a test account called “attacker@778899gmail.com” I invited myself to the platform. Then, I explored the User Manager option to see what information I could find.
There we got some basic info about the invited user like name, login, email… Here the login field is responsible for password change, But I was not allowed to change the login and email field of the invited user.

I intercepted the request and attempted to modify the login parameter, hoping it would give me Account Takeover to the invited user’s account. Unfortunately, my plan didn’t work out as expected. However, I didn’t give up just yet.
So I went to change the Email address to “victim778899@gmail.com” by intercepting the request and to my surprize it actually changed the email address of the invited user on the front-end as well as on back-end.
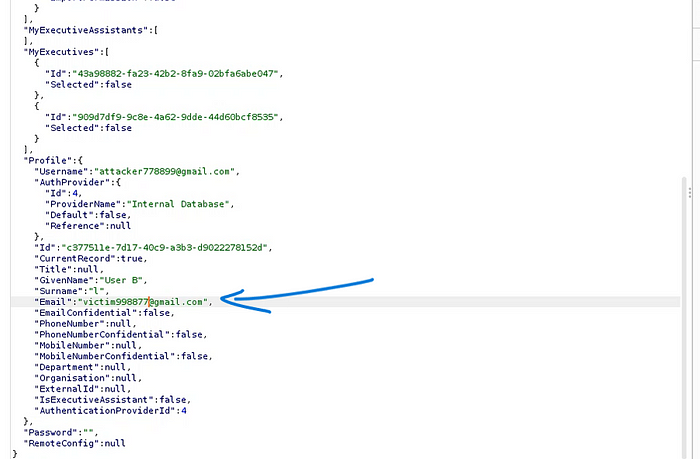
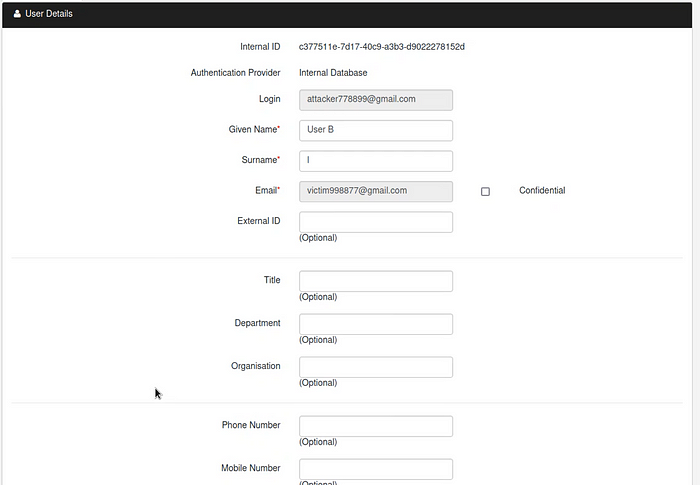
I know this is a Low Severity bug, but this is an intresting find for me, So I couldn’t resist sharing this writeup with all of you.
Impact:
This vulnerability can lead to Per Account Takeover of any unregistered user and an attacker can misuse the identity of the victim.
Timeline:
25-March-2023 >> Bug Reported
20-June-2023 >> They patched the vulnerability & marked it as low severity.


